I talked at length in my article
Investing in Real Convergence
about my decades-long wish to have a single computer I could carry with me that had all of my files, ran all of my favorite programs, and that I could use as a mobile computer, laptop, or desktop. This past week I have finally realized that dream.
I put away my personal Librem 13v1 and tested out whether I could replace it with a Librem 5, USB-C hub, and Nexdock 2 laptop dock. I also spent a couple hours most work days trying it out for work as well (including writing this article from the Librem 5). In this article I will talk about my setup, experiences and impressions from the past week.
The Setup
First let’s talk about the hardware involved.
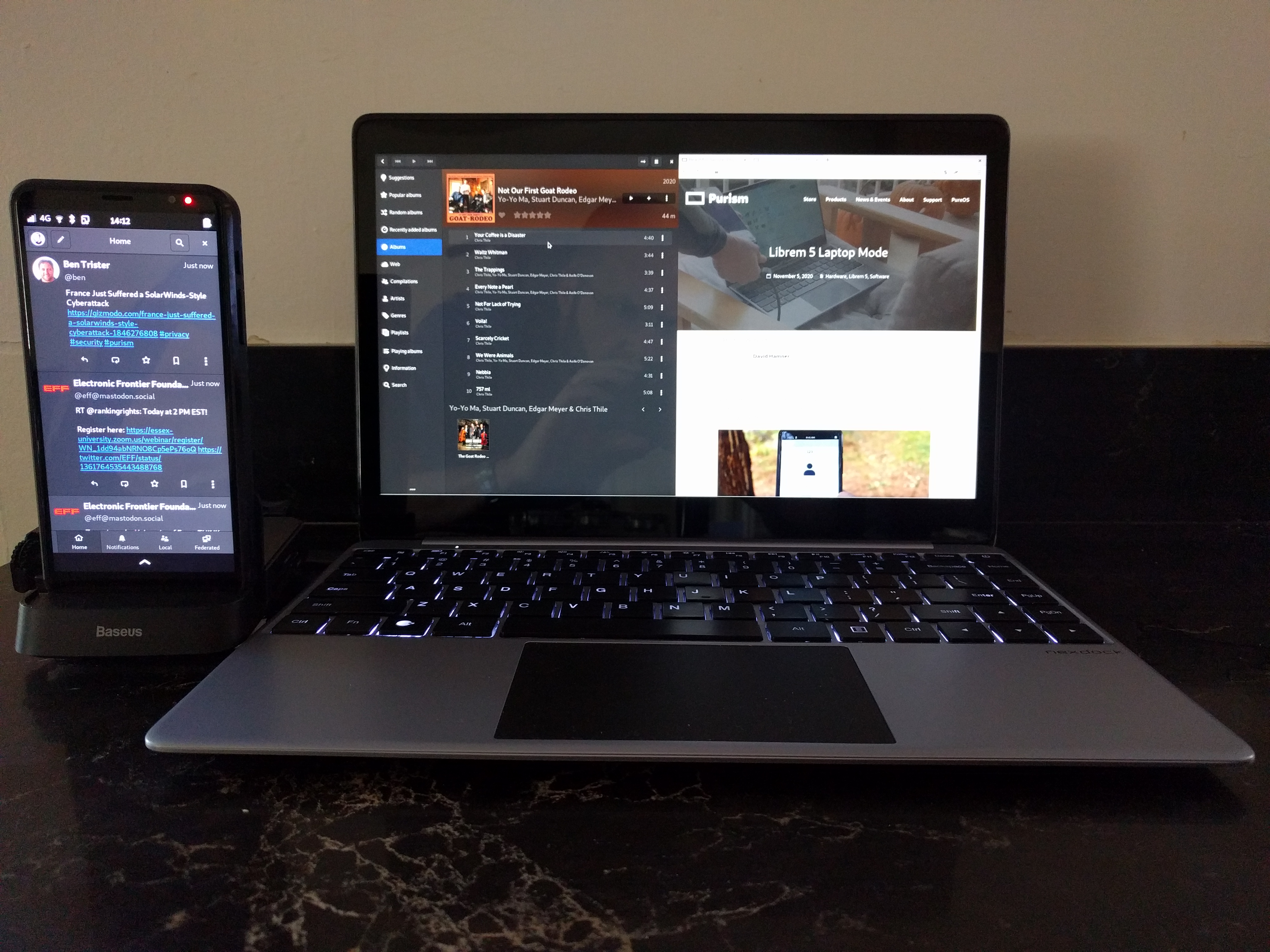
Librem 5 docked to a Nexdock 2 using a Baseus USB-C hub, running Tootle, Lollypop, and Firefox
The first thing that is necessary for this setup besides the Librem 5 itself is a laptop dock. From the outside, a laptop dock looks just like a regular laptop, but it is really only a shell with a display, keyboard, mouse, internal battery, and a few ports on the side. A laptop dock has no CPU, RAM, storage or networking of its own and instead is designed to act like an all-in-one monitor, keyboard and mouse that you can connect to a phone. The phone then extends onto the display and you can run your phone’s applications on the larger screen and take advantage of the physical keyboard and mouse while the dock charges your phone.
Because the Librem 5 is designed to have
Real Convergence
, it runs the same PureOS applications as Librem laptops. All of its applications were simply adapted to work well on the smaller display. This means when you connect the Librem 5 to a laptop dock or monitor, you don’t just get phone apps blown up two times their size, you get the same desktop PureOS applications as on Librem laptops.
On laptop docks like the recent Nexdock Touch, you can connect the Librem 5 directly to the dock with a USB-C cable. In the case of the older Nexdock 2, the support isn’t completed yet so I used the foolproof method they provide for other computers like Raspberry Pis–a HDMI port and USB-C port–only in my case I connected them to a Baseus-branded USB-C hub that is well-supported by the Librem 5.
This hub provided the extra benefit that it kept the Librem 5 upright, which was particularly important to me since I actually use my laptop on my lap. To make this work with the dock I simply attached the underside of the hub to the underside of the laptop dock with a small metal bar and some removable 3M tape like you’d use to mount pictures to a wall.
Using Convergence Mode
To use the Librem 5 like a laptop, I just dock it into the USB hub and press the power button on the laptop dock. The Librem 5 detects the keyboard, mouse and display and automatically enters “convergence mode” which extends the desktop to the new display and changes the windows so that they have close buttons on them and aren’t automatically maximized, so they can be more easily moved between desktops.
Once in convergence mode you can drag applications over to the larger screen with a mouse, however there are also already a number of useful key bindings using the “Super” key (the key between the left Fn and Alt keys) that make convergence mode very keyboard friendly:
-
Super + (Left|Right): Tile the focused window to the left or right side of the active screen
-
Super + Shift + (Left|Right): Move the focused window to the left or right display
-
Super + (Up|Down): Maximize or unmaximize the focused window
-
Super + a: Open the App Launcher, where you can type in the name of the application to launch, or select it with arrow keys
-
Super + s: Open the App Switcher (similar to hitting the bottom section of the touchscreen on the phone). This allows you to switch between running applications using the arrow keys
While in convergence mode, the dock is keeping the phone charged. I found the Nexdock 2 could run for about two to three hours of steady use unplugged while powering its own display, the hub, and charging the Librem 5. It lasted longer if I closed the display when I wasn’t using it. Since the laptop dock is powered via its own USB-C port you could extend this time with a large battery bank if you didn’t have access to an outlet. Since I normally use my laptop from the same place every day, I tend to leave it plugged in anyway.
When I’m done using the Librem 5 like a laptop, I just remove it from the hub and it automatically leaves convergence mode. All of the running applications move back to the phone screen and resize and maximize to fit. The laptop dock automatically powers itself down.
My Experience
I don’t do video editing or other heavy tasks on my laptop and for the most part my needs are pretty simple: web browsing, chatting, email, writing, listening to audio and watching video. In many ways even before this experiment my Librem 5 had already replaced my personal laptop. It had already become the primary computer I used for podcasts and videos (using gPodder and VLC), as well as for social media and light web browsing. That said, I still found myself opening my laptop in the past whenever I needed to type more than a few sentences in chat, an email, or a document. I also found it a bit more convenient to do heavier web browsing (like when researching something across multiple tabs) on a larger display.
Given my relatively simple use case for my personal laptop, I had high hopes that the Librem 5 could replace it and
the Librem 5 didn’t disappoint
. In fact, what I found was that the addition of a laptop dock made the functions I had already moved over to the Librem 5 even more useful. With a large screen, I could more easily multitask, such as chat in one window while a video was playing in VLC tiled to the side of the large screen. The addition of a physical keyboard also made chat, email, and overall writing much more convenient.
I found that I preferred the multi-monitor setup that convergence mode defaults to and use both screens at the same time. I leave certain applications like my social media applications or gPodder on the phone screen. Then terminals, email, web browsers, chat applications, and video playback would be on the laptop screen with windows tiled either to the left or right-hand side.
Since the phone is close to my left hand, I found I use the phone touch screen to interact with applications there instead of the mouse. It’s convenient to reach over and scroll through new social media posts on the phone screen instead of moving the mouse over. The fact that the Nexdock touchpad defaults to multi-finger scroll that moves in the opposite direction of the Librem 13 touchpad took a lot of getting used to.
I tend to be keyboard-centric on my regular laptop and this is no different on this setup. I made heavy use of the existing keybindings along with alt-tab to switch between and manage windows. After a short amount of time I got used to hitting Super-a, typing the name of an application, and hitting Enter, then hitting Super-Shift-Right or Left depending on which screen I wanted it on. I find the keyboard to have good tactile feedback and while it’s no Model M keyboard (but
sigh
, what is?) it’s pleasant to type on and better than some island keyboards I’ve tried.
My Impressions
The Librem 5 can definitely replace my personal laptop
and I’ve already transferred any remaining files from my laptop over to it, powered down my laptop, and put it away. My laptop has a faster CPU and more RAM, so I expected when I used the Librem 5 like a laptop I might more readily see any performance differences it might have compared to using it like a phone.
I have to say, though, that this Librem 5 surprised me in how well in performs, in particular how well it works when multi-tasking between applications. Web browsing works surprisingly well, and although I do typically keep Firefox in “mobile mode” so I get lighter weight websites designed for a mobile browser, I actually prefer that mode on the larger screen as it often results in cleaner, simpler web pages.
While it’s still early days for phosh acting as a full desktop shell, it already works quite well in that mode. While it’s not as full featured as the default GNOME shell on the desktop, many of the basic important features are already there (since they are already there when in phone mode) and work as you might expect on the larger screen. As more of us use the Librem 5 in convergence mode now, we are seeing rapid advances for the desktop use case.
My hacky USB hub mount works surprisingly well and is strong enough to hold up the weight of the phone while the laptop dock is on my lap, but I also make a point not to put too much extra pressure on it, just in case. While I’ve seen other mounting options that attach a phone to the screen, I find I like having the phone’s touchscreen within a closer reach.
One area that’s a bit less convenient is the extra step of having to dock the Librem 5, open the laptop dock lid, and power it on to switch to “laptop mode” compared to just opening the lid of a suspended laptop. It’s a minor inconvenience though, since I just use the Librem 5 in “phone mode” for quick tasks anyway–if I’m breaking out the laptop it’s for a longer session. For people who would use the phone in “desktop mode” connected to a monitor and keyboard/mouse, it wouldn’t be any less convenient than docking their laptop into a docking station.
Using the Librem 5 for Work
Something that surprised me even more was how well the Librem 5 performed to replace my work laptop. My work use case is a bit more complicated than my personal one, mostly due to the security requirements. Otherwise for the most part my primary work tasks involve email, chat, and web-based tools, along with some writing and light development work from time to time.
I should note that my work laptop is a Librem 13v4 with twice the RAM of my personal laptop because I make heavy use of Qubes and its compartmentation features on my work laptop to provide me extra security. I separate chat, web browsing, email, and other functions into separate VMs that can’t directly talk to each other. I also make heavy use of disposable VMs whenever I have to open a potentially risky document or website. Because of those extra compartmentation features Qubes provides, I don’t know that the Librem 5 could replace my work laptop, yet, but wow is it
close
.
Now that the
OpenPGP smart card reader is supported
, I copied my Purism GPG subkeys over to a new smart card and migrated my email settings over to the Librem 5 along with my password manager database for work. I also set up a new compartmentalized web browser with its own profile and settings that I used only for work.
Email works just like it did on my work laptop. Web browsing and web tools also work reasonably well. Chat is probably the main area that, today at least, still needs a bit of work to replace my work laptop, due to the fact that Matrix with e2ee support is still under heavy development. I’m actually trying out an experimental branch of Chatty that contains support for encrypted Matrix chat, but it’s not quite ready to replace a traditional client.
My conclusion for work is that the Librem 5 as it is today would at least be able to replace the need to take my work laptop with me when traveling. Fully replacing my work laptop would probably need to wait until we make further advancements in flatpak sandboxing using bubblewrap, so I have some of the protections I’ve gotten used to in Qubes that give me extra peace of mind.
Welcome to the Future
Using a phone that has real convergence like the Librem 5 is a complete game changer. It feels like I’m getting a sneak preview into the future of personal computing. In many ways it’s hard to explain what it’s like, you kind of have to see it yourself to understand why this is so groundbreaking. Having all of the same desktop applications and all of my files with me in my pocket, and having those same running applications morph to a larger screen automatically, changes how you think about phones and their potential.
Calling the Librem 5 a phone doesn’t do it service. It’s really a mobile computer, a desktop in your pocket. Using it like a laptop or desktop computer really opens your eyes to all of the possibilities, and underscores to me all of the things I’ve been missing with other phones.
Discover the Librem 5
Purism believes building the Librem 5 is just one step on the road to launching a digital rights movement, where we—the-people stand up for our digital rights, where we place the control of your data and your family’s data back where it belongs: in your own hands.
Order now
The post
My First Week of Librem 5 Convergence
appeared first on
Purism
.
 chevron_right
chevron_right



 Librem 5 docked to a Nexdock 2 using a Baseus USB-C hub, running Tootle, Lollypop, and Firefox
Librem 5 docked to a Nexdock 2 using a Baseus USB-C hub, running Tootle, Lollypop, and Firefox